
Versa Titan SD-WAN FEATURES
Carrier Grade NAT
Carrier Grade NAT (CGN/CGNAT), also known as Large Scale NAT (LSN), is an approach to IPv4 network design in which sites are configured with private IPv4 addresses that are then translated to public IPv4 addresses using a centralized device to manage the address translation to the public internet. This process shifts the Network Address Translation (NAT) function and configuration from the premise to the cloud.
Stateful Layer 4 Firewall
Firewalls can operate at different layers of an Open Systems Interconnection (OSI) model depending on filtering. In a Layer 4 Firewall this is done on port numbers and keeps track of the source and destination ports. It monitors the connection state and sequence numbers. The conversations can only be initiated by internal hosts – which is accomplished by keeping a state table or a dynamic session table to track all conversations and only packets matching the rules in the state table can pass through the firewall.
Stateful inspection eliminates the need to create new rules. For traffic initiated in one direction, you do not need rules that permit traffic in both directions. For example, The client traffic that is initiated in one direction includes Telnet (port 23), HTTP (port 80), and HTTPS (port 443). Client computers initiate this outbound traffic; you create a rule that permits outbound traffic for these protocols. Stateful inspection automatically permits the return traffic that responds to the outbound traffic. Stateful means that you only need to create rules that initiate a connection, not the characteristics of a particular packet. All packets that belong to an allowed connection are implicitly allowed as an integral part of that same connection.
Denial of Service
Denial of Service (DoS) is a malicious attack on a network – designed to bring a network to its knees by flooding it with useless traffic. Many DoS attacks work by exploiting limitations in the TCP/IP protocols.
Hackers use DoS attacks to prevent legitimate uses of computer network resources. DoS attacks are characterized as attempts to flood a network, disrupt connections between two computers, prevent an individual from accessing a service or disrupting service to a specific system or person. Those attacked my lose e-mail services, internet access or web servers. DoS attacks may eat up bandwidth or even use all of a system resource, such as server memory, for example.
Site to Site IP sec VPN
Site-to-Site IPsec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches). The VPN tunnel is created over the public Internet and encrypted using a number of advanced encryption algorithms to provide data confidentiality between the two sites.
Site-to-site VPNs connect entire networks to each other. In a site-to-site VPN, hosts do not have VPN client software; they send and receive normal TCP/IP traffic through a VPN gateway. The VPN gateway is responsible for encapsulating and encrypting outbound traffic, sending it through a VPN tunnel over the Internet, to a peer VPN gateway at the target site. Upon receipt, the peer VPN gateway strips the headers, decrypts the content, and relays the packet towards the target host inside its private network.
Dynamic IPSec Overlay
Dynamic IPSEC VPN Overlay is the dynamic IPSEC tunnel established between branches. When you bring two branches connected to the controller, the controller acts as a route-reflector client exchanging the branch information to the other branches as IPSEC-SAs, L3VPN routes etc. Based on the IPSEC-SA received, the branches will establish the Dynamic IPSEC with all the other branch nodes. This is how branch to branch communication will happen via the IPSEC tunnel
Traffic Load Balancing
We provide a rich set of Layer 4 (L4) Load Balancing (LB) advanced capabilities, usually based on source and destination IP addresses and ports recorded in the packet header.
Our Load Balancing provides (LB) Virtual IP Addresses (VIP) and implements translation between VIP and Real IP Addresses mux’ing/demux’ing between multiple servers or network destinations using translation tables. This includes various load-balancing algorithms (including RR/WRR, source or destination hash, least connections, etc.) while supporting UDP and TCP based Health Monitoring and Source and/or Destination IP Address persistence techniques. This capability allows the NaaS solution to implement native service chaining abilities that provide flow persistency and service chain load, aware of LB, capabilities towards any physical or logical 3rd party components.
Application Visibility
Port numbers, protocols, and IP addresses are useful for network devices, but tells us very little about their customers’ networks. Detailed information about the applications, users and content on the network empowers us to quickly determine any risks and respond accordingly.
Application Traffic Management, SLAs, Application Shaping and QoS
Application Policy Based Traffic Forwarding (PBF), Application Traffic Engineering (TE), and Application Quality of Service (QoS) are an extensive set of traffic management capabilities available in the Versa Titan SD-WAN solution.
Using App-QoS, a rich set of QoS capabilities can be implemented per application flow like; marking, rate limiting, prioritization, drop profile assignment and management, adaptive shaping, hierarchical queuing, etc., to help manage and prioritize links and paths in the most effective ways starting from application priorities and expanding to application bandwidth and SLA requirements.
Using App-PBF, manage customer application flows based on extensive policy match / trigger conditions with extensive set of policy enforcement functions, including forward, forward to service chain, and apply security profiles with a rich set of nexthop override functions, etc.
Using App-TE implement a rich set of application traffic flow management capabilities based on link, path, flow performance, delay, jitter, and packet loss characteristics that change dynamically. App-TE/App-SLA Management capabilities allow network operators to serve applications in the best ways based on changing network dynamics.
Migration Gateway
To transform Customers’ legacy networks to SD-WAN networks, our customer need Migration Gateways. This gateway allows translation between different packets and exchange reachability information across different protocols. It also provides means to monitor and implement application traffic identification and steering functions to and from the legacy network.
Adding SD-WAN to an existing WAN infrastructure is simple. During the migration, all existing WAN equipment, services and connections, continue to operate as before. While it’s possible for us to replace existing WAN infrastructure, creating a virtual WAN overlay doesn’t require a forklift upgrade of existing routers or infrastructure at branch locations. In other words, customer can start migrating customers immediately and migrate them at their own pace, without disruption.
Versa Titan can have multiple active links in a Active/Active state these links can be Broadband,4G- LTE, MPLS or IPSEC tunnel. Active-active mechanism based on link performance provides protection against blackouts and brownouts with sub-second failover. Provider and physical link diversity ensures high availability
Easy to use management
Inline Loss Management
Versa Titan will continue sending SLA Pdu’s between Branches WAN-links. For example, two branch nodes each have two WAN-links. For every configured interval we will send SLA Pdu’s between these wan-links. Based upon the SLA-Pdu reception we will determine the loss, delay, jitter etc., between these Branches. These are called SLA parameters. We considers the SLA Pdus and the actual data packet to determine the loss percentage between any two nodes. We also calculates the loss percentage in the actual data flow between two branches’ data traffic – known as Inline Loss Management. Based upon this loss percentage we will determine which WAN-link to choose for sending data.
Packet Striping
Versa Networks enable customers’ same speed interfaces like a bundle so that the SD-WAN solution can make most use of the bandwidth across a cumulative set of links. This is necessary if a site has a lot of slow speed links or paths.
Versa Titan uses per flow load balancing, which addresses more than 90% of use-cases. In the case of “elephant flows,” per packet load balancing can create a high utilization or even overflow on slow links while the rest of the links may be underutilized.
To address this, Versa Titan also provides the ability to load balance per packet across a bundle of links or paths. Once this feature is enabled, the packet flows will spread across the bundle while assigning a sequence number to each packet. This will help all member links to be used uniformly. The receiving side will use the packet sequence numbers to ensure the streams will be regenerated at the right packet sequence order and sent to their destination(s) accordingly.
Forward Error Correcting (FEC)
Versa Titan SD-WAN forward error correction (FEC) technology can regenerate dropped packets on calls where up to 25 percent of packets are dropping. It inserts a loss-recovery packet with a signature after every four packets, and any missing packets can be regenerated using the signature number. This eliminates unnecessary packet retransmission, further reducing latency and enabling a better customer experience.
Forward Error Correction (FEC) is a digital signal processing technique used to enhance data reliability. It does this by introducing redundant data, called error correcting code, prior to data transmission or storage. FEC provides the receiver with the ability to correct errors without a reverse channel to request the retransmission of data.
The central idea is the sender encodes the message in a redundant way by using an Error Correcting Code (ECC). The redundancy allows the receiver to detect a limited number of errors and often correct these errors without retransmission. FEC gives the receiver the ability to correct errors without needing a reverse channel to request retransmission of data, but at the cost of a fixed, higher forward channel bandwidth. FEC is therefore applied in situations where retransmissions are costly or impossible, such as one-way communication links and when transmitting to multiple receivers in multicast
Packet Cloning
Realizing that degradation could occur during transport due to packet loss or even the robustness of the network on which its traveling, Versa Titan SD-WAN takes steps to ensure calls make it to their intended destination in good shape. Packet cloning, for one, replicates traffic across all defined links so the receiving SD-WAN node is guaranteed to get all packets, even if part of the packets’ journey is less than ideal. Once the packets are received and put in their proper order (thanks to the packet identifier at the head of each packet), the clones are discarded. This is ideal for VoIP as the overhead of voice packets is low and marginal
SD-SECURITY FEATURES
Next Generation Firewall & Unified Threat Management
The most vulnerable point of an enterprise is the branch office – these offices usually don’t have IT on-site and use various kinds of transport (i.e. business class internet, broadband, MPLS, Ethernet, LTE, etc.) making it difficult to integrate networks and security products across these multi-site networks.
Gartner estimates that more than 30% of advanced threats will target these branch offices.
Software-based security functions increase branch security and simplify operations – right away eliminating two of the biggest security hurdles – limited IT staff and complex network integrations. This software-defined approach to security leverages a virtualized network and functions that run on commodity hardware.
The Versa Titan software-based security solution enables you to provide a variety of functions, maximize cost efficiency, and simplify operations for your customers through zero-touch provisioning and automatic service chaining.
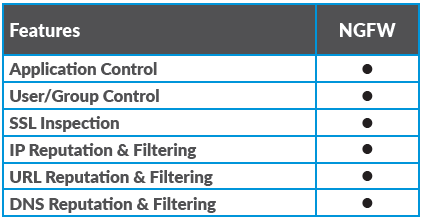
URL Categorization, Filtering and Control
Virtual Customer Premise Equipment (vCPE) / SD-Security solution provides a rich set of URL Categorization and Filtering Capabilities to screen web traffic to see if it poses a security risk, is out of compliance with company policies, if it needs to be filtered for parental control, or if it needs to be authenticated / authorized further for access or for another purpose.
This solution comes with more than 80 predefined URL categories that allow customer to quickly manage customer URLs by category, trustworthiness, confidence level, etc. In addition to predefined classes, Versa Titan also provides user-defined / custom classes that can be created and managed as needed.
These capabilities are key to providing safe and compliant network services to enterprises. With the added benefit of granularity of users and user-groups – different actions can be taken on top of the URL like, allow, alert, drop session/packet, reject, ask, justify, block and override.
L7 Access Control
The Application Access Control feature provides the ability to manage and secure application traffic flows using a very rich set of application traffic policies. The Versa Titan solution recognizes traffic flows of more than 2,600 applications and maps them to major and sub-classes helping manage flows of each application.
Application Access Control capabilities include allow, deny, restrict access, redirection, captive portal based application access management, logging, and other advanced actions like scripting. Combined with User and Group Level Access Control, Application Access Control gives tremendously powerful capabilities to network operators.
URL & IP Reputation Feeds
The NGFW includes a market leading integrated URL and IP Reputation solution that provides an effective management of traffic destined to URL or IP Destinations based on systematically collected opinions of a world-wide community of users.
When used in combination with URL Filtering, URL and IP Reputation ensures that traffic – using the community of user’s experiences – does not visit questionable or out of compliance sites. The URL & IP Reputation feeds are updated periodically to reflect changes in the Internet environment and community of users. This feature is also very effective in suppressing C&C virus or malware traffic that could be planted in user’s machines or within their content.
User/Group Access Control
The Versa Titan NaaS solution has built-in User and Group Based Control capabilities, enabling a whole new dimension of security and policy control based on user and user-group credentials. The NaaS solution integrates with Active Directory through LDAP and Kerberos mechanisms, gets the user and group information and applies security, and access.
User & group focused security and control policies also allow the creation and execution of user & group specific services like, parental guidance, enforcement of company compliance, access & authorization policies, and policies tailored for specialized users such as executives, guests, contractors and more.
With this policy dimension, SD-Security & SD-WAN extend out to cover industry leading multi-dimensional policy based decisions like routing policies, application policies and URL & IP reputation with user & group information, which allows the most extensive and powerful set of policies to be defined and executed on the user’s traffic

Anti-Virus Protection
Through the Versa Titan UTM solution, we provide customer with a rich set of embedded antivirus capabilities using multilayered techniques like: heuristics, signature matching and emulation. Our Antivirus solution uses lower CPU and memory resources, achieving efficient resource utilization and optimized cost points. Antivirus signatures get updated frequently – this also updates the FlexVNF instance, allowing customer to have access to the latest virus signatures, helping them protect their customers’ networks most effectively.
Intrusion Detection & Intrusion Protection
As part of UTM, we provide Intrusion Detection System (IDS) and Intrusion Protection System (IPS) solutions that allows customer to monitor their networks for malicious activities and policy violations that can originate from inside or outside the network. IDS/IPS features provide a robust set of detection, prevention, logging and reporting capabilities, as well as serving as a tool to detect out of compliance users and applications.
The Versa Titan IDS/IPS solution comes preloaded with various attack profiles tailored for various OS, server and client profiles, and using these profiles, IDS/IPS features will implement pattern matching algorithms to detect and prevent attacks, ensuring the information integrity and protection of the customers’ networks.
SSL & TLS Inspection
Versa Titan UTM solutions provide Secure Sockets Layer (SSL) – which is the standard technology for keeping an internet connection secure and safeguarding any sensitive data – and Transport Layer Security (TLS) – which is an updated more secure version of SSL – decryption capabilities to enable the resellers to apply consistent application, security, content and compliance policies for encrypted traffic flows.
SSL and TLS capabilities provide application based optimized decryption capabilities for SMTP, HTTPS, SSH and other traffic flows. This implementation allows public and private keys to be managed with appropriate RBAC, ensuring proper management of decryption profiles.

